Influencers: US should sanction China for economic espionage
Loading...
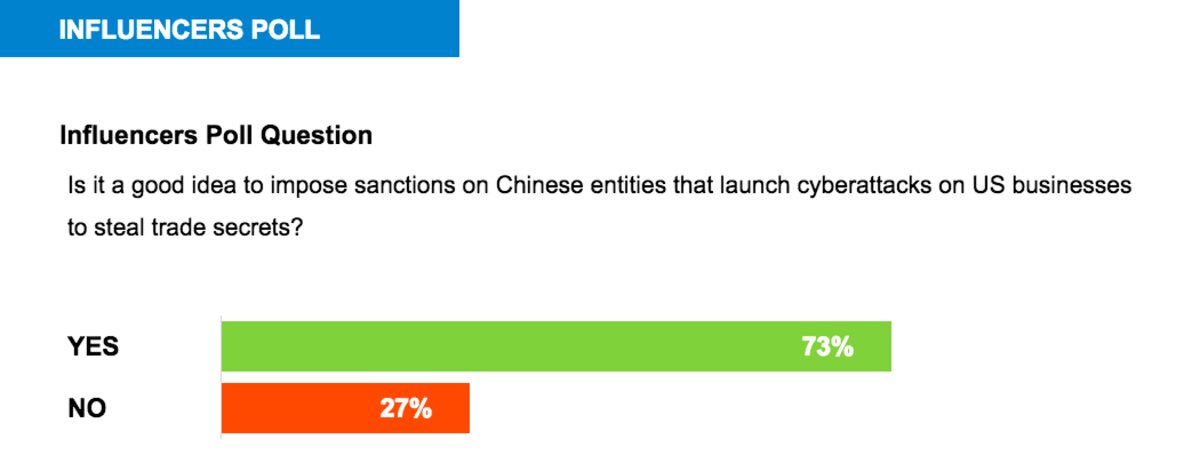
The US should impose sanctions on Chinese entities that launch cyberattacks on American businesses to steal trade secrets, a strong majority of Passcode’s pool of digital security and privacy experts said.
The Obama administration is reportedly developing a raft of sanctionsagainst Chinese companies that have benefited from the theft of US intellectual property, along with individuals who orchestrated the cyberspying. Economic espionage is expected to be a hot topic as Chinese President Xi Jinping visits Washington later this month, in the wake of high-profile hacks of US businesses; China is also the lead suspect of the massive Office of Personnel Management breach.
As Washington considers how to respond, 73 percent of Passcode’s Influencers said sanctions aimed at curbing China’s economic espionage would send the right message.
“Thus far, our diplomatic and other efforts have not made a dent in stemming the flow of intellectual property from US businesses,” said Dmitri Alperovitch, cofounder and chief technology officer of security company CrowdStrike. “We need to start considering new approaches to put pressure on Chinese companies to stop stealing and begin competing fairly in the global marketplace.”
Passcode’s Influencers Poll is a regular survey of more than 120 experts in digital security and privacy. They have the option to comment on the record or anonymously to preserve the candor of their responses.
The US says it does not participate of corporate espionage — using its intelligence and national security apparatus to spy for the benefit of American businesses — for moral reasons. And yet, Representative Jim Langevin (D) of Rhode Island said the costs of corporate espionage to the US is “real and massive, and present a serious threat to our long-term economic and national security.”
There has been “no sign the hacks targeting the American economy are abating,” Rep. Langevin continued, despite the Obama administration’s diplomatic outreach and a federal indictment last year of Chinese military hackers targeting US companies in the nuclear power, metals, and solar products industries.
“More aggressive action by the administration, including the imposition of sanctions, is overdue,” Langevin said, noting there could be a need for an even stronger response down the road: “I hope that they will be enough to induce China to stop its campaign of theft and cheating and join the community of responsible nations in cyberspace, but if they are not, I will support further proportional retaliatory measures.”
Since the US would need to prove the targeted organizations were involved in illegal conduct in order to impose sanctions, said Jay Healey, a senior research scholar at Columbia University’s School of International and Public Affairs, the move would ratchet up the pressure.
“The sanctions are not against ‘China,’ but the specific entities involved in the theft of trade secrets,” Mr. Healey said. “This is directly targeting those involved in the illegal conduct, locking them out of US markets or refusing them visas. So while it is certainly escalatory, it is less so than counter-hacking or other aggressive state versus state action.”
Still, a 27 percent minority of Passcode Influencers said US sanctions would not be the most effective tool against Chinese espionage.
“Sanctions run the risk of an ever increasing escalation of retaliation but will do little or nothing to stop state sponsored espionage,” said Cris Thomas (aka Space Rogue), a strategist at Tenable Security. “Sanctions do, however, work to help silence the critics that accuse the administration of doing nothing.”
Instead, he said, the correct response by the US government should be to ensure all its agencies are implementing basic security controls. “Things like knowing what is on the network, who has root access and when it is being used, and what the patch levels are. These basic things will not prevent espionage, but will make the effort much more difficult.”
There are also some risks to imposing sanctions for digital espionage, experts said. For instance, without properly verifying the attackers’ identities, the US runs the risk of falsely blaming, and punishing, China. For its part, China routinely denies that it carries out corporate espionage.
“This is a complex issue.... For sanctions to be imposed there have to be two things. Clear attribution of the attack to the entity against which sanctions are being made, and disclosure of the facts that have led to the decision to impose sanctions,” an influencer, who chose to remain anonymous, said. “The level of sophisticated forensics required to determine attribution should not be underestimated, nor should the desire to keep such forensics secret.”
The emphasis in US policy, the influencer continued, “needs to shift to resilience and deterrence at that level rather than sanctions. This, combined with increased political collaboration, is a better way to deal with the cybertheft of trade secrets.”
What do you think? VOTE in the readers’ version of the Passcode Influencers Poll.
Who are the Passcode Influencers? For a full list, check out our interactive masthead here.
Comments: Yes
“This seems like a prudent escalation beyond the previous indictments of members of the Chinese military. Increasing measures are needed to make it clear that the US will not stand for unbridled cyber theft of valuable US-based intellectual property.” — Ely Kahn, Sqrrl
“While I think sanctions are appropriate when the US has conclusive proof that foreign governments attacked US business systems, I don’t they will be effective or particularly meaningful. First, businesses need to get to at least a due diligence/basic hygiene level of security - most courts would call those compromised systems ‘attractive nuisances.’ Secondly, the US is trying to make a fine distinction between ‘bad’ cyber intrusions and ‘OK’ cyber intrusions, based on whether the goal was political or economic. The two are not separable anymore.” — John Pescatore, SANS Institute
“It’s a good idea but you must be extremely confident in the attribution, it needs to be made public, and the Chinese government must be told ahead of time what is going on and exactly why. This is one of those steps that is needed but there cannot be any miscommunication.” — Influencer
“We have to come to grips with attaching consequences to actions, the recent EO [executive order] sets a standard of ‘malicious cyber activity’ but it has yet to be applied in practice.” — Influencer
“The challenge is attribution. Attackers using Chinese IP space may not be Chinese at all. The US also has to be prepared for sanctions for US cyber activities that the Chinese think are sanction- worthy.” — Chris Wysopal, Veracode
“But only if attribution is assured. Unfortunately, that is much more difficult than most policy makers understand.” — Influencer
“A good idea but extremely difficult to implement. How do you know which entity launched the attack? Attribution in cybersecurity is a hard problem.” — Influencer
“We are losing the cyberwar. Our national security and the privacy of every American are in serious jeopardy. We must act with equal seriousness.” —Jenny Durkan, Quinn Emanuel
“President Obama signed an executive order in April giving the administration the ability to sanction entities worldwide for engaging in cyberattacks against US targets. If the US has undeniable proof that China has undertaken a cyberattack and the administration sees such a response as a tactic that will have more positive than negative impact then it should follow through on its promise to respond to such attacks.” — Influencer
“The present dynamic is cost-free to the attackers, so let’s create some costs to those profiting from the attacks. It also creates a few useful concession points to end for negotiations in the future.” — Influencer
“There have been exactly zero costs imposed on China for their proliferate hacking of the US (and every other country in the world with any digital property worth stealing). It’s long past time to impose some costs for their behavior; something is better than nothing.” — Influencer
“Malicious actions deserve repercussions. It’s taken the U.S. government far too long to converge on a cost-imposing solution to such unacceptable behavior in cyberspace.” — Amy Chang, Staff Director of a House Foreign Affairs Subcommittee
“There are serious privacy, cybersecurity, and commercial competitiveness risks and the consequences should be appropriately calibrated. Imposing sanctions is a better alternative than is hacking back, which could have unintended consequences.” — Influencer
“The US needs to create international norms and an agreed-upon framework for responses to cyberattacks. Unilateral action would be a disaster without that rule of law, and the US, in particular, is in a position to help drive this much-needed update to international law.” — Sascha Meinrath, X-Lab
“Among other things, deterrence requires a credible response capability and a willingness to deploy it. Cybersecurity doesn’t turn deterrence theory on its head, but there’s more nuance here given that all nation states with the technical capacity engage in cyber-espionage. Stealing corporate trade secrets to benefit local industry, however, should be sanctioned to create credible deterrence. The challenge then is how to do so in the big picture of relations between two super-powers. In this case, there are probably small-scale and perhaps escalating responses (diplomatic protest, low-level trade tools, etc.) that can demonstrate a willingness to respond. The USG should also continue to emphasize, as should industry advocacy groups, that one key to China’s long-term success economically will come from genuine and organic competition and innovation in the market.” — Influencer
“Chinese leaders do not perceive the US as having the political will to impose sanctions for Chinese theft of commercial secrets from Western companies. If the US wants to change China’s subjective interpretation of the situation, the administration must change the objective facts. Sanctions are needed to impose visible, public costs on Chinese companies and individuals who benefit from stolen commercial secrets.” — Richard Bejtlich, FireEye
“My general position is that the US needs to impose sanctions on any entities that are attacking U.S. companies, citizens and government. That goes beyond China.” — Influencer
“But not before the summit and with providing more evidence than in the past.” — Adam Segal, Council on Foreign Relations
“However, I think we should first exhaust all forms of diplomacy.” -Influencer
“Economic espionage is different in character and nature from national security ‘covert action’ espionage and should be treated differently. Economic sanctions for economic crimes is a proportional response where all sides know the rules of the game.” — Jeff Moss, DEF CON Communications
“We certainly already know that it isn’t a good idea not to,” — Influencer
“Yes, but it is very difficult to consistently perform accurate attribution of network attacks to specific attackers. An IP address is not a person. Consequently, it isn’t clear what fraction of the overall attack activity can be addressed with this particular approach.” — Bob Stratton, MACH37
“Yes, but not the ones being discussed. Rather than tying up their ability to move money in some way that depends on our side having a continuing, workable ability to do so, I would do something more along the lines of simply de-routing all their addresses (both now known and to be discovered) for some fixed time -- much like a jail sentence that says you will sit outside society until we tell you you can return. We won’t get restitution from Chinese firms because we won’t apply the kind of civil forfeiture to them we routinely apply to minor and not-so-minor thugs here at home. We have, for better or worse, come to require numerous safety – and security – relevant services from [Internet Service Providers] and though I don’t like that (end-to-end is better design than safe pipes), ISP regulation is what we institutionally have to work with. Just de-route the miscreants. Of course, the miscreants may be using stolen or misappropriated assets of otherwise blameless third parties, so the question becomes whether we de-route the third parties as well and/or provide the third parties with material assistance in taking action against said Chinese perpetrators on their own behalf and, by extension, ours. In any case, a combination of shunning and surveillance is what I recommend, assuming, as the Passcode question itself assumes, that we can’t get today’s or tomorrow’s victims to just buck up their damned defenses to levels that makes this whole mess go away. Getting someone else to go after perps is what you do when you are fully invested in being a mark.” — Dan Geer, In-Q-Tel
Comments: No
“’Trade secrets’ are pretty low level stuff and they get ‘stolen’ all the time. That’s a business model problem, not a foreign policy problem. But if you asked me about the theft of patented intellectual property, and told me that there was a persistent pattern of theft, then I’d say that the US government would (and should) consider imposing sanctions regardless of how the theft occurs -- cyber or dumpster diving for example. In other words, what gets stolen to me is more important than how it gets stolen.” — Steve Weber, UC Berkeley
“My primary reason for hesitation is the difficulty of precise attribution, though the lack of historical effectiveness of sanctions on behavior is also a factor.” — Influencer
“Sanctions always have unintended consequences. If they restrict trade then the damage done will ricochet against US consumers and businesses.” — Richard Stiennon, IT-Harvest
“The lack of positive attribution makes this a dangerous game - too much opportunity for false flag attacks.” — Influencer
“Sanctions will fail to accomplish their objective of stemming the flow of cyber attacks from China, and it will harm US businesses who do business there. Google, who pulled out of China in 2010 for cyberespionage reasons is now returning for financial reasons. That tells you all there is to know about why this sanctions plan is lose-lose for US companies.” — Jeffrey Carr, Taia Global
“Slippery slope, there are other ways to handle the problem.” — Influencer
“The problem with the US imposing sanctions on China for economic cyberespionage is that the Chinese don’t understand the US position that there is a difference between economic espionage - which the US claims it does not do - and national security cyber espionage, something the US does daily. The line seems arbitrary to the Chinese culture. ...The truth is, key players on the international stage believe what China believes. France is notorious for industrial espionage, and the Russians, until recently, have just been stealthier about their operations, compared to their Chinese brethren...The real question is not whether we should distinguish between industrial cyber espionage and state secret cyber espionage. The real question is what do we do about cyber espionage in general. … After the Cold War and since the Internet has become the ubiquitous access tool it now is, the change in espionage has been one of scale. Before the Cold War, spy organizations stole secrets one at a time at considerable peril to their secret agents in the field. After, cyber spies can now hoover up libraries of secrets from the safety of their own living rooms. China, Russia, and France understand this and believe it would be silly not to take advantage of the situation. Imposing sanctions on countries for pursuing this activity would not stop it. Most countries would consider it the cost of doing business. The libraries of hoovered secrets would be worth the price. So, sanctions are not the answer. What might work are incentives. We need to find ways that make it mutually beneficial to all players not to conduct cyberespionage operations. I am not sure what those might be, but I am positive that the U.S. imposing sanctions on China will have no effect and will just raise tensions between the two countries.” — Rick Howard, Palo Alto Networks
“The US leads the world in cyber-hypocrisy, always playing the victim when it’s really the most cyber-aggressive country in the world, the only country to launch a true cyber war attack, Stuxnet, against Iran. Rather than cyber retaliation, we should be discussing cyber disarmament.” — James Bamford, Foreign Policy Magazine
What do you think? VOTE in the readers’ version of the Passcode Influencers Poll.