What is the right way to prevent breaches?
Loading...
Organizations need a prevention-based approach to cybersecurity. Doubling down on detection and response will only continue to lead to costly breaches and harm to companies and consumers. Indeed, organizations need to strike a balance between prevention and detection/response capabilities.
The first step is to define the word “prevention.” True prevention means no damage has been done and there is no need for remediation because the attack has been prevented. Detecting that an endpoint has been compromised and then attempting to do something about it (quarantine, network isolation, etc.) is not prevention. This is detection and response. Detection and response is a key capability in your toolbox as a last resort, but if your capabilities are all based on this detection/response approach, you are at a clear disadvantage.
Ultimately, the adversary is interested in compromising an endpoint. The network is often a vector of attack and thus strong network security has the potential to thwart the attack. However, if the attack is not stopped on the network, or does not arrive via the network, the endpoint is the last line of defense when it comes to preventing targeted, advanced threats.
Thus we need a new approach to prevent compromise of our endpoints, the laptops, desktops, tablets, servers, and other connected devices that make our enterprises run. The anti-virus and anti-malware products we have all relied on for decades are clearly not up to the task.
To help shed light on this new approach, we teamed up with the research group Forrester to ask organizations what they are doing to address this challenge. In particular, we asked what types of prevention-based endpoint protection technologies they have adopted and what features and capabilities are most important to them. Then we delved further into what’s working and what’s not working in regard to each of those approaches.
In this revealing paper, Forrester highlights the results of the study and provides a set of recommendations to organizations seeking to define a new strategy geared toward prevention of zero-day exploits and unknown malware. The full report can be found here.
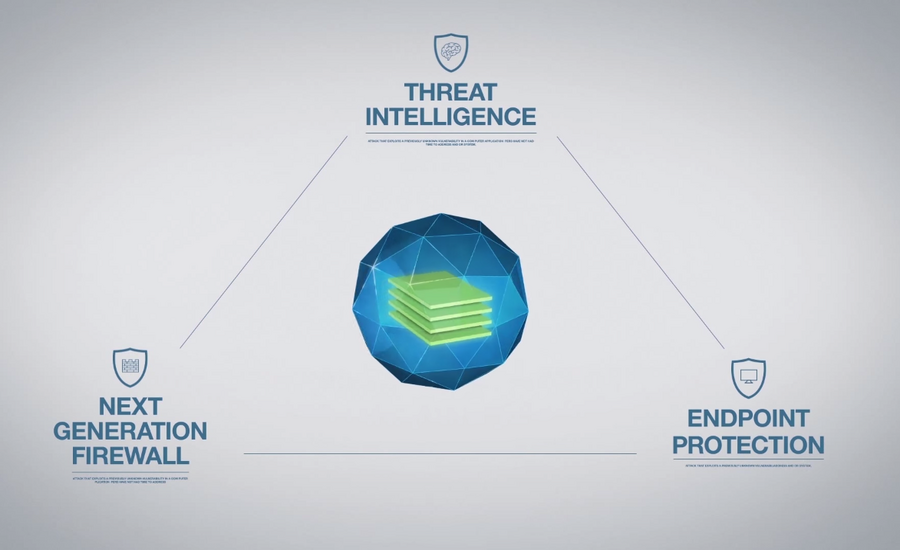
The bottom line? A comprehensive prevention strategy involves three key elements:
- A natively-integrated platform that includes next-generation network security, advanced endpoint protection, and shared threat intelligence.
- The ability to prevent zero-day exploits and unknown malware on the endpoint, without waiting for a signature or other type of update.
- Balance, in the sense that security should not require a disproportionate sacrifice of operational efficiency or end-user performance.
With the expansion of Internet-connected devices, it is clear that security professionals across all industries will need to focus more on prevention in the coming years. When cyber attacks cross into the physical world, such as in the case of internet connected cars, after-the-fact measures are no longer an option. It is imperative that the prevention mindset, as well as related technological innovation, take hold and become mainstream as we advance toward our increasingly connected future.
Sebastian Goodwin is director of product marketing at Palo Alto Networks. Follow him on Twitter @SebGoodSF.