Influencers: US plan to limit export of software vulnerabilities a bad idea
Loading...
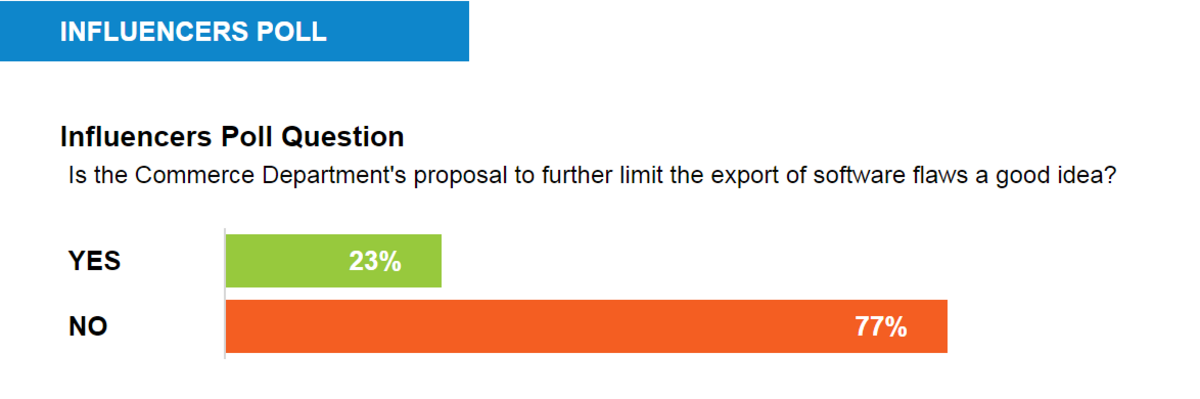
A strong majority of Passcode's Influencers oppose a new proposal by the US Commerce Department to further restrict the export of most software vulnerabilities.
While the changes to the Wassenaar Arrangement, the 41-country agreement that governs arms exports, were offered in large part to help block the export of military-grade spyware to repressive regimes, 77 percent of Passcode's Influencers worry the new rules could, as an unintended side effect, hinder legitimate analysis of computer security weaknesses.
"While the goal of protecting people from malicious software and exploits is noble, these restrictions will do nothing to prevent the use of malware by authoritative regimes and will seriously affect legitimate security research," says Alex Stamos, Yahoo's chief information security official.
The Commerce Department's Bureau of Industry and Security guidelines are "tremendously overbroad, and appear to prohibit the sharing of vulnerability research without a license," says Electronic Frontier Foundation Executive Director Cindy Cohn. "This is incredibly dangerous; the same tools that are used to attack systems are also the ones we need to help discover flaws and attacks. BIS says it doesn't want to hurt vulnerability research, but its rules go much further than Wassenaar requires and further than other countries go. The result could be a complete backfire, making technologies we all rely upon less secure." (This week, BIS said its proposal was intended to curb the export of tools to control or develop what it deems intrusion software, but the technical clarification appears to have done little to assuage experts' concerns.)
Passcode's Influencers Poll is a regular survey of more than 100 experts in digital security and privacy who have the option to comment on the record or anonymously to preserve the candor of their responses.
Influencers are concerned the proposed rules will also have unintended consequences for technical innovation, which, according to Katie Moussouris, chief policy officer for HackerOne, "conflicts with the mission of the Commerce Department, in that it will serve to create a competitive disadvantage for US businesses because of new export licensing overhead, that ultimately does not serve the intended purpose of controlling surveillance software."
Even the Chamber of Commerce isn't on board quite yet. "For example, would technologies commonly used for penetration testing information systems get caught up in the export-control net (which seems unwise from a security standpoint)? How would BIS judge software used by multinational companies that monitor their overseas networks? How would the policy impact individuals that take their laptops overseas — would these devices need licensing?" asks Matthew Eggers, its senior director in the National Security and Emergency Preparedness Department. "Thought needs to be given also to how the proposal would act as a drag on timely threat information sharing. The US Chamber would like to learn about the experiences (pro and con) of other parties to the Wassenaar Arrangement before seeing BIS move ahead."
Some experts also worry the US government is miscalculating the effects on national security. "Controlling zero-day exploits can be a good idea. But using export control perpetrates the idea that zero-days are part of a national arsenal, that they should be nurtured for offensive value, not discovered and fixed," says Jay Healey, senior research scholar at Columbia University's School of International and Public Affairs and senior fellow at the Atlantic Council, referring to the type of software flaw exploited by hackers before the vendor realizes can fix the problem. "Yet again, US policy starts with a valid risk and ends up with a militarized solution."
What's more, says Chris Doggett, managing director of Kaspersky Lab North America, "looking at the current cybersecurity landscape and rapidly increasing sophistication of today’s threat actors, it’s evident that the bad guys will be able to navigate around any regulatory controls that we might put in place. Even if further limitations on the export of software flaws are introduced, they will likely prove to be ineffective at deterring nefarious individuals from utilizing the black market to monetize their discoveries because the risk/reward equation will still be very attractive."
Perhaps even more concerning, Doggett adds, is if legitimate researchers are restricted from sharing their discoveries across national borders, the proposals "could have the net effect of leaving end users – or worse, government and critical infrastructure – open to more attacks than would otherwise occur. This would happen if such legislation had the effect of tying the hands of the good guys while at the same time prove unsuccessful at stopping the bad guys. As a result, while we should make equipping our adversaries with powerful weapons illegal, we must be very careful about any legislation is written so that we don’t do more harm than good."
However, a 23 percent minority of Influencers say the proposed changes, which are open for public comment until July 20, are a good idea – with some caveats.
"No US citizen should be selling information on zero-day exploits to our nation's adversaries," says Daniel Castro, vice president of the Information Technology and Innovation Foundation. "That said, the US has some of the best security minds in the world. If they discover flaws in software made by foreign companies, they should be able to sell information about those flaws to the makers of that software or claim any bounties. The market for software vulnerabilities incentivizes more security research. The Department of Commerce should not cut off this valuable economic activity."
Who are the Passcode Influencers? For a full list, check out our interactive masthead here.
What do you think? Take the readers version of the Passcode Influencers Poll.
Comments: No
"It will have a larger negative effect on security researchers than it will on criminals." – Martin Libicki, RAND Corporation
"The unrestricted sale of exploit tools is a serious concern, as these tools can be misused in the hands of repressive governments. The problem with the proposed regulation is that it has the potential to disrupt good-faith security research as well, by targeting specific technologies rather than behaviors." – Matthew Green, Johns Hopkins Information Security Institute
"Since all – repeat, ALL – software contains flaws, any proposal to limit the export of flawed software is an attempt to limit exports, period. Let the market sort out what software is superior (including number of flaws) to another rather than bureaucrats attempting to impose their necessarily sub-optimal understanding on the global market." – Influencer
"This is an irrelevant and largely unenforceable concept that will have little to no practical impact on security and distract us from marshalling focus of effort on items that can move the needle." – Amit Yoran, RSA
"As currently proposed by the US Government, and the BIS in particular, there is cause for grave concern that these measures may have a significantly negative impact on national security. It is unclear whether the national security benefits envisioned by the drafters would actually outweigh the potential damage. Both a reading of the proposed export rule changes and recent comments by BIS Director [Randy] Wheeler may reasonably cause one to wonder whether the US Government is drawing some arbitrary (and undisclosed) distinction between 'vulnerability research' and 'exploits, zero days, and intrusion software' that is in no way distinct, understood by the affected technology developers and users, or for that matter, even articulable. Most security professionals would agree that this class of software and techniques will play an increasing role in the overall body of capabilities that may find application in the context of international conflict. Unfortunately, to add yet another hindrance to the rapid detection, disclosure, and remediation of IT vulnerabilities is far more likely to impair efforts to secure what DHS calls the "Homeland Security Enterprise" than it is to harden it against adversaries." – Robert Stratton, MACH37
"I think this is a weak attempt at solving the much bigger problem of export controls for cybersecurity technology. The export system for cyber needs a complete overhaul, not a Band-Aid." – Influencer
"Just as the US has no monopoly on crypto expertise, and crypto export controls make no sense, the same is true for zero day flaws and penetration testing tools. Export controls will make it harder for US security vendors and have no impact for all those finding and selling vulnerabilities outside the US." – John Pescatore, SANS Institute
"While well-intentioned, the proposed rules will likely only discourage white hat collaboration and drive unscrupulous vulnerability researchers further underground. Instead, the government should encourage more disclosures and collaboration by sharing more of its publicly-funded vulnerability research findings and methods." – Chris Finan, Manifold Security
"In much the same way that 1990s export controls made the international transport of laptops with the strong encryption contained in most web browsers illegal, the proposed Commerce Department export rules would sweep up a host of incredibly useful research – criminalizing entirely useful and productive activities – due to its over-broad language." – Sascha Meinrath, X-Lab
"This is the cyberworld. There's no possible way to police this." – Influencer
"Notionally, this is worth exploring. As currently drafted, however, the proposal can cause more harm than good. Hopefully, that's where the requirement for notice, comment, review, and revision come in. Stay tuned!" – Influencer
"The BIS interpretation is super overbroad, even of the already expansive Wassenaar Agreement. It's bad that countries are using malware to attack citizens, but how open security research is critical to security." – Influencer
"I only clicked 'no' because 'it depends' wasn’t an option. The devil will be in the details – it will come down to how BIS and other agencies interpret these new controls. We must ensure that they do not stifle security research and innovation, which would be inconsistent with the original intent. Implemented poorly, they could hurt cybersecurity both in the US and abroad – precisely the opposite of what they should do." – Jeff Greene, Symantec
"Banning the foreign sale of the fruits of dual-use computing research will cause great damage to an arcane but necessary industry that is vitally important to the defense of our mainly privately-owned critical infrastructure. To legislate ignorance of computer vulnerabilities by criminalizing an industry in which global competition thrives at the level of private enterprise and nation-states is short-sighted, naive and will ultimately cause more harm than good." – Nick Selby, StreetCred Software
"Software attack tools ... can literally be built by anybody who has a laptop, a compiler and a mindset that is keen to understand how things work and how one might subvert an original design for other purposes. They do not have to start from scratch either. The basic designs of Stuxnet, Flame and DuQu are readily available on the Internet. It would not take much for a small team of modestly resourced hackers to build their own. Buying exploits to feed your attack platform would not be hard either. The underground economy for exploits has been around since the Internet was a collection of tin cans and string. These new export rules will not affect that in the least. By implementing the 2013 Wassenaar Arrangement rules, the only thing you accomplish is making it harder for legitimate commercial organizations to sell their products and services abroad. In other words, if one of the Defense Industrial Based companies wanted to sell their internally developed attack platform to Iran, the Wassenaar Arrangement members would know. I guess that is something but it puts a burden on these companies without coming close to accomplishing the goal: prevent bad actors from getting attack platforms." – Rick Howard, Palo Alto Networks
Comments: Yes
"The sale of software flaws has always been a controversial topic. It's based upon the theory that sharing that information improves our overall security however the number of breaches by way of exploiting known or newly discovered vulnerabilities seems to be increasing every year. Therefore, I think we need to look at alternative measures such as the one put forward by the State Dept. Perhaps less sharing is what we need, rather than more." – Jeffrey Carr, Taia Global
"If the new BIS [regulations] promote transparency and responsible transfers of dual-use tech by limiting export of software flaws (which it appears they would do, at least in principle), then they're aligned with the purpose of the Wassenaar Arrangement. Seems many researchers disagree with the transparency point, so it will be interesting to learn more during the comment period." – Michael Samway, Georgetown University
"Conceptually, it's a great idea. However, Commerce does need to be careful that it's not overly broad in what it defines as a vulnerability. There are ample opportunities in the process to finalize these rules for Commerce to address some of the concerns that have been raised." – Influencer
"It's a start. We've still got a very long way to go in designing a workable system of responsibility (which doesn't necessarily mean liability!) for software distribution." – Influencer