Android security flaw puts millions of users at risk
Loading...
A newly discovered vulnerability in the Android operating system could expose hundreds of millions of smartphone and tablet users to malicious software, according to research from a cybersecurity firm.
Palo Alto Networks said Tuesday that it uncovered a vulnerability that could give attackers control over a mobile device and access to data, usernames, and passwords via seemingly benign applications downloaded from third-party stores such as the Amazon Appstore. Apps downloaded from the Google Play store are not affected.
The potential harm of the bug that security company has named "Android Installer Hijacking" is vast: more than 1 billion people worldwide are active Android users. Palo Alto Networks said it informed Google of the problem a year ago, and worked with Google, Amazon, and Samsung, which also has a popular Android app store, to release patches. So far, however, there does not appear to be any known evidence that hackers have exploited the bug to attack mobile phones and tablets.
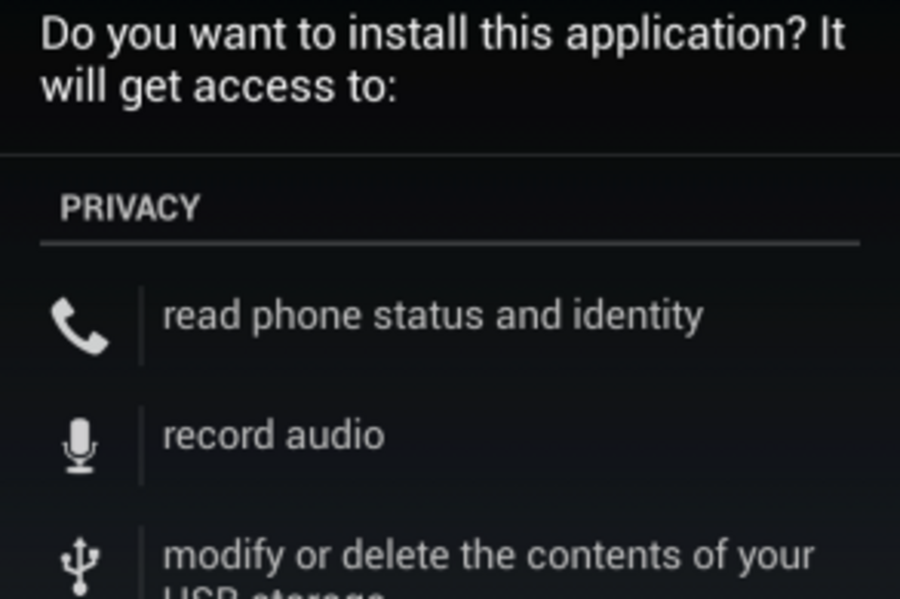
Android Installer Hijacking works by tampering with the installation process, allowing an attacker to install any program in place of the app a user thinks they are installing. This could mean one app is replaced with a completely different app or, worse, a seemingly harmless app is replaced with a more malicious version of itself. The vulnerability does this by circumventing the permissions process, which allows users to limit how apps interact with the phone.
Android is designed so that an app alerts users during installation if it intends to use the microphone, tracks the mobile device's location, place calls, or uses other core features of their devices. But hijacked phones might install one program while offering the alerts for another app's function.
"The danger is that this vulnerability allows all privileges to be installed regardless of what permissions users were told about," said Ryan Olson, director of Palo Alto Networks' Unit 42 Intelligence Lab, the company's research division.
Users are still able to view permissions after the installation.
Android versions earlier than 4.4 can be affected. Though Google patched the 4.3 version, Palo Alto Networks found a number of smartphones shipped without the patch installed. Palo Alto Networks has developed a free app so that Android users can check if their phones are at risk.
Traditionally, the chief security concern with Android (as opposed to the Apple smartphone operating system) has come from Google Play's minimal app screening process. In the past, Google Play did not screen apps for malicious software the way that Apple's App Store has. Recently, Google announced it would start doing just that.
In the past, however Android has seen other vulnerabilities allow one app to masquerade as another: In 2014, the security firm Bluebox discovered a way to spoof security certificate verifying apps on Android.
Google did not respond to a request for comment.