The Pentagon is building an app store for cyberoperations
Loading...
It looks like outer space.
The hundreds of thousands of computers look like stars. Across the vast military network, the sparkling connections between them form constellations.
This is the Pentagon's vision of the Internet.
The US military's cyber warriors, unlike soldiers patrolling a battlefield overseas, will not hear the sound of an attack coming. They will not see their opponents in the flesh. They will not die because they were in their line of fire.
Like information security professionals at private companies, they spend long hours hunkered over computers, analyzing lines of code, trying to detect breaches – a laborious process that requires advanced engineering skills. Though their networks are scanned up to millions of times every day, there is no alarm system that triggers when an enemy hacker crosses a virtual tripwire to breach their network. There’s no virtual explosion if they destroy the data inside.
The Pentagon's research arm wants to change this.
With a project called Plan X, the Defense Advanced Research Projects Agency (DARPA) is building what could one day become a virtual reality that gives cyber warriors "instantaneous knowledge of the fact [their] network is being attacked," says its program manager Frank Pound.
Slated to cost around $125 million over four years, Plan X marks the first major attempt to create an actual online battle space and would fundamentally shift the way the military operates on the virtual battlefield.
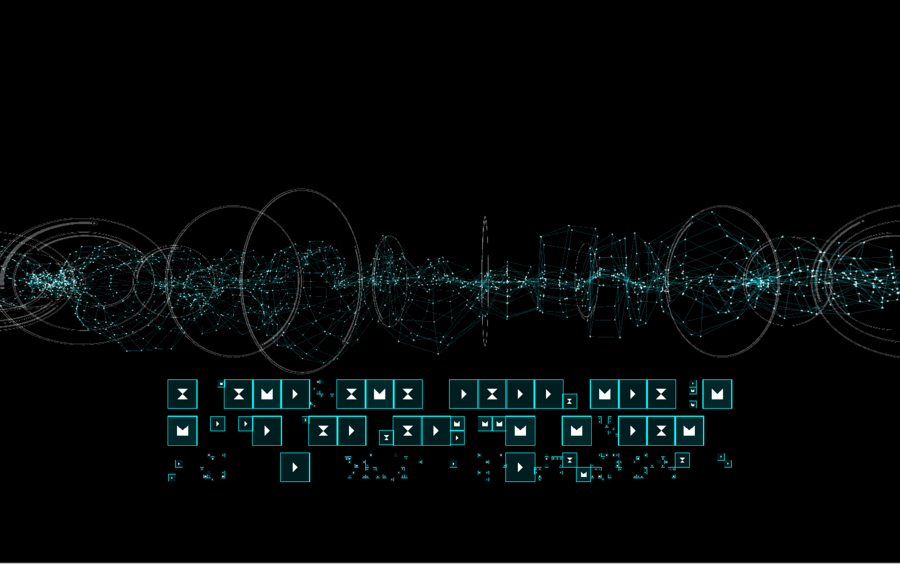
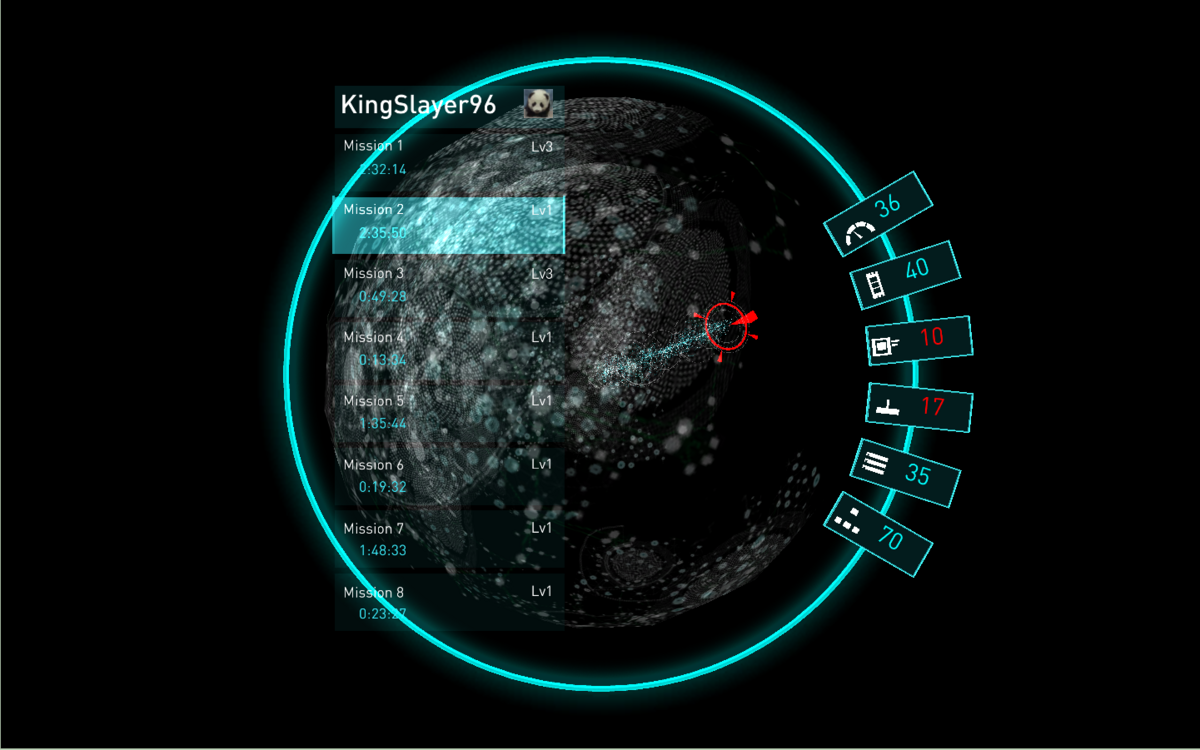
Simply moving a hand across a flat, touchscreen monitor could allow a user to analyze the health of the entire network or find rogue computers that are not supposed to be connected. Attacks would be translated into rich display graphics and 3-D visualizations so it's impossible to miss them as they happen. Military specialists could defend against them by literally dragging blocks of code from a virtual shelf or marketplace similar to Apple’s App Store onto their network. They may one day even use 3-D visors like the Oculus Rift, a video-gaming headset, to launch these operations in a fully immersive virtual reality.
Here's why this is a big deal: Protecting its networks from computer attacks is as important to the military as defending the country's air, land, sea, and space. The director of national intelligence has listed a potential compromise of online systems and theft of information as the No. 1 threat to US national security – more than terrorist groups or weapons of mass destruction. US military superiority, as Chairman of the Joint Chiefs Martin Dempsey said recently, does not carry over into cyberspace. It may have superior weapons and technology, but the asymmetrical nature of cyberconflict means increasingly sophisticated attackers will always have the upper hand against the defenders.
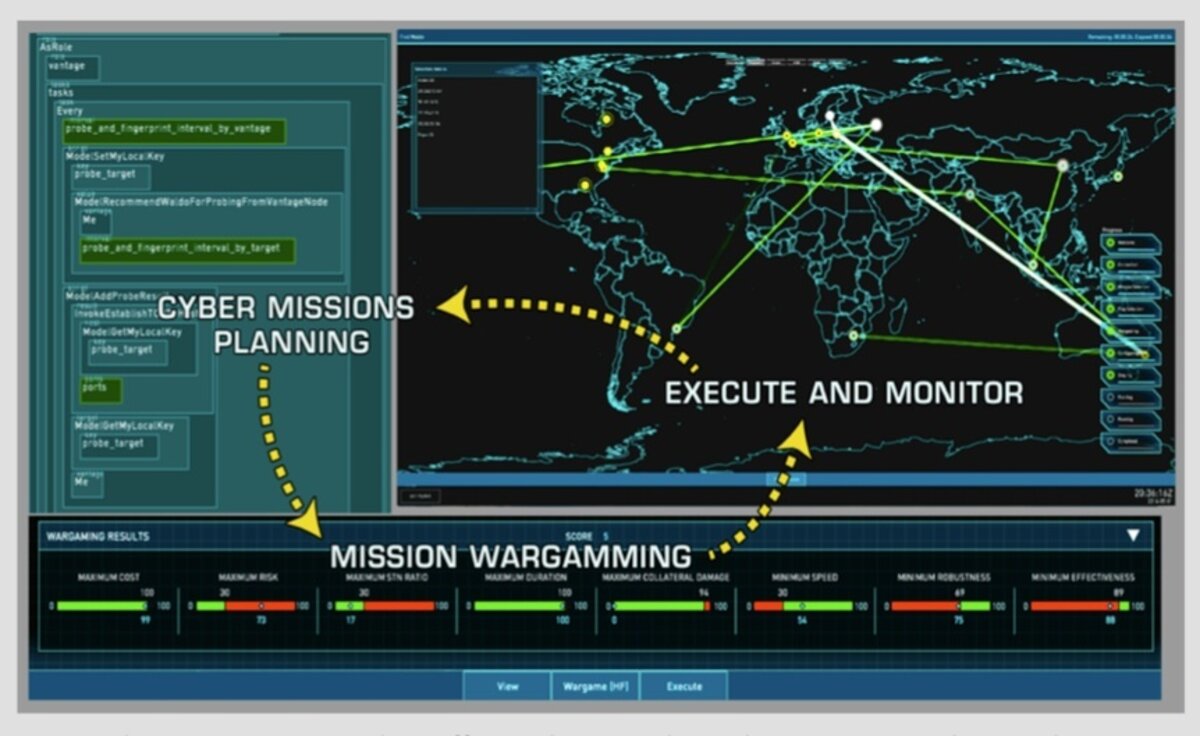
A program such as Plan X would also speed up the military’s cyberoperations. With it, researchers expect it to take up to 72 hours to write, test, and deploy a mission – a process that, at this time, sometimes takes months.
The program is still in the early stages, but DARPA is the influential agency that fueled the creation of the Internet in the first place. It also invented the technology behind GPS, videoconferencing, and other key tools you likely use every day. It's possible that one day Plan X could ultimately end up in your hands to help track the health of all the devices in your home network.
Passcode, The Christian Science Monitor's new section on security and privacy in the Digital Age, has the exclusive first peek at the Plan X concept.
Editor's note: DARPA's Frank Pound will also give a live demonstration of Plan X at a Passcode event on the future of cybersecurity innovation in Washington, D.C., on Feb. 26. Join us.
The military wants to give defenders the advantage
"Typically when networks are attacked full scale, leading up to that months beforehand, what may be buried in lots of log data that nobody noticed are certain types of packets that are hitting your network," Mr. Pound says. With the real-time analytics DARPA is building into the Plan X system, cybersecurity personnel would be able to see those anomalies emerge before a full-scale attack. "You’d be prepared for that," he says.
There’s a reason DARPA wants Plan X to be so intuitive. The Pentagon announced last year it would triple the number of its cybersecurity professionals to 6,000 by 2016. Training highly skilled workers in a technical field en masse is no easy feat, especially since companies globally are struggling to fill their information security jobs quickly enough. "Another goal of Plan X is to not require people to have computer science degrees and go through years of training," Pound says.
Even the personnel they do have might not be enough to combat the rapidly increasing level of sophistication and frequency of intrusions onto the vast US military networks.
"It takes a lot of skill to get to the point where you can look at streaming network, packet data scrolling across a screen, and be able to pick out that one packet of information that may be malicious,” Pound says. “It’s not very intuitive. It’s very hard to understand.
"What we’re doing is building big database technologies that support real-time streaming of this network data and real time analytics – smart analytics – that can weed through all that data and only present to the end user, the operator, things that are important for him or her to see," he says.
One vision of how this would work – and what it would look like – goes something like this:
The scene: Twenty-five to fifty years in the future.
A woman in a gray bodysuit, with a blonde pixie cut, holds a flat screen tablet. She's tracing the origin of a cyberattack.
Then – an arc of fire emanates from a hostile computer.
An alert flashes across the screen.
Her network was breached.
Liberty, the woman, represents a cyber warrior of the future.
She is the main character in a storyboard developed for DARPA by the San Francisco-based concept and design company Massive Black.
That particular concept for Plan X was tabled – at least for now – in favor of a simpler design.
But the striking graphic display of a network breach shows DARPA’s thought process as it aims to represent hacks visually, in a way humans will be able to intuitively understand.
DARPA is in the middle of studies to determine what kind of shapes and iconography humans understand best, as it decides how to visually represent the Internet, Pound says. For this challenge, DARPA has recruited a team that includes former video game designers, and people who worked in Las Vegas developing the computer-based slot machines.
So it’s possible there one day could be a virtual tripwire and ensuing explosion to signify network compromise. For instance, Pound says, "Should we make the icons catch on fire? Is that the best way to do that?"
The agency may also build graphics into its system to show users if their countermeasures against attacks are working.
In the storyboard, for instance, Liberty quickly isolates part of her network from the attack hurtling toward her home network. The red fiery arc melts away. The cyberattack was rebuffed.
Before there can be images to depict cyberoperations, there must be accurate words to describe them.
The military already has icons that represent tanks, battalions, and adversaries. The Plan X team is taking the limited pool of cybersecurity icons that exist and building it out to represent the full range of computer attacks, from distributed denial of service attacks, meant to to overwhelm a network with a high volume of traffic, to man-in-the-middle attacks that intercept private communications.
The challenge: Representing different types of attacks in ways the human users can understand and differentiate them. It's not enough to say that a DDoS attack is taking place, because they come in many different forms. A network can be attacked from a single computer, with one connection. Or, hundreds of computers and connections could target the network.
It's not possible to build Plan X with images when there’s no rigorous set of terms that describe the nuances of different types of computer attacks, defenses, and parts of the network, however. That's why DARPA is creating its own.
"Until we come up with this good common way to discuss and describe cyberoperations, cyberattacks, and cyberbehavior, we're not going to get very far," Pound says.
"So if you build an ontology you start having a common language, a common lingo to talk about things -- and that translates into a rigorous semantics. Sort of like legalese. When you go talk to an attorney or you go before the court, there’s a certain protocol where you speak to the judge," he says.
In essence, the programming code must be translated into a comprehensive set of jargon before it can be automatically displayed as a graphic for the humans to interact with.
Making Plan X easy for people to use is its own challenge.
DARPA is heavily experimenting with a 55-inch flat touchscreen, responsive like an iPad. It's working with designers who specialize in making devices easier and more intuitive, for instance, people who have designed cameras on consumer electronics.
This team watches people use different devices and surveys their preferences.
"They'll have people turn wheels, move things across, and they'll film it and go back and say, 'She had to reach way too far over there to get to that component on the desktop that she uses all the time, maybe we should add it over here so there's no reaching or wondering where those things are,'" Pound says.
With Plan X, Cyber Command could write operations to store as apps in a database.
"Just like the Apple App Store," Pound says.
The goal is to eliminate as much typing as possible. At crunch time, Pound says, "you don't have to worry about where the semicolon goes."
All the military’s cyberoperations, from checking the health of its networks to defending against different kinds of cyberattacks, are currently written in code. In Plan X, those operations would appear in the form of pre-programmed, block-style apps loaded in a store-like platform accessible to all the partners in the system.
When a network is probed or a hack attempted, Pound says military officers can solicit help from within the Plan X system, asking their counterparts for contingency plans to address the threats.
"They’ll be able to write their own apps to do their own analytics, their own operations and share these things with the collaborative interfaces that we’ve built," Pound says. "It may be that an analyst at Cyber Command shares an app with Army Cyber."
To launch the operation, the cyber warrior would simply pick one of these apps and drag it into the network on a touchscreen device.
If there’s an extra dump of malicious traffic on a certain segment of the network, for instance, Pound says there might be a pre-written app that would shut down a router and redirect traffic to another part of the network – even turn it into a honeypot, or decoy. The military could segregate the part of the network that appears to be targeted from the rest of its systems; put in extra filters to guard against the malicious code, or spread the information across multiple servers in different locations in a practice known as load balancing.
It might not stop at defense, either, as virtually any operation the US wants to use could be written as an app into the Plan X system. "Think about Plan X as an aircraft carrier or a fighter plane," Pound replied. "The bombs and all that stuff come from somewhere else. This is just the framework."
While certain apps would require higher authorization – perhaps from higher-ranking military personnel – to deploy, how the operations are used on Plan X all depends on what the government wants to use it for.
Eventually, the goal is for Plan X to incorporate some modicum of artificial intelligence. The system will understand what the user is interested in.
"It's similar to some of the websites you go to, where a banner ad says, 'Hey, you might be interested in these shoes today because you shopped for shoes earlier,' " Pound says. If a user surveyed all its operating systems to make sure they had the latest updates, for instance, Plan X will remember that mission. The system will say, according to Pound, " 'Hey, you ran this scan on your network to find out if all your machines were patched, Plan X ran that scan again to make sure ... . Here are the results for you.' "
Commanders want Plan X for the battlefield.
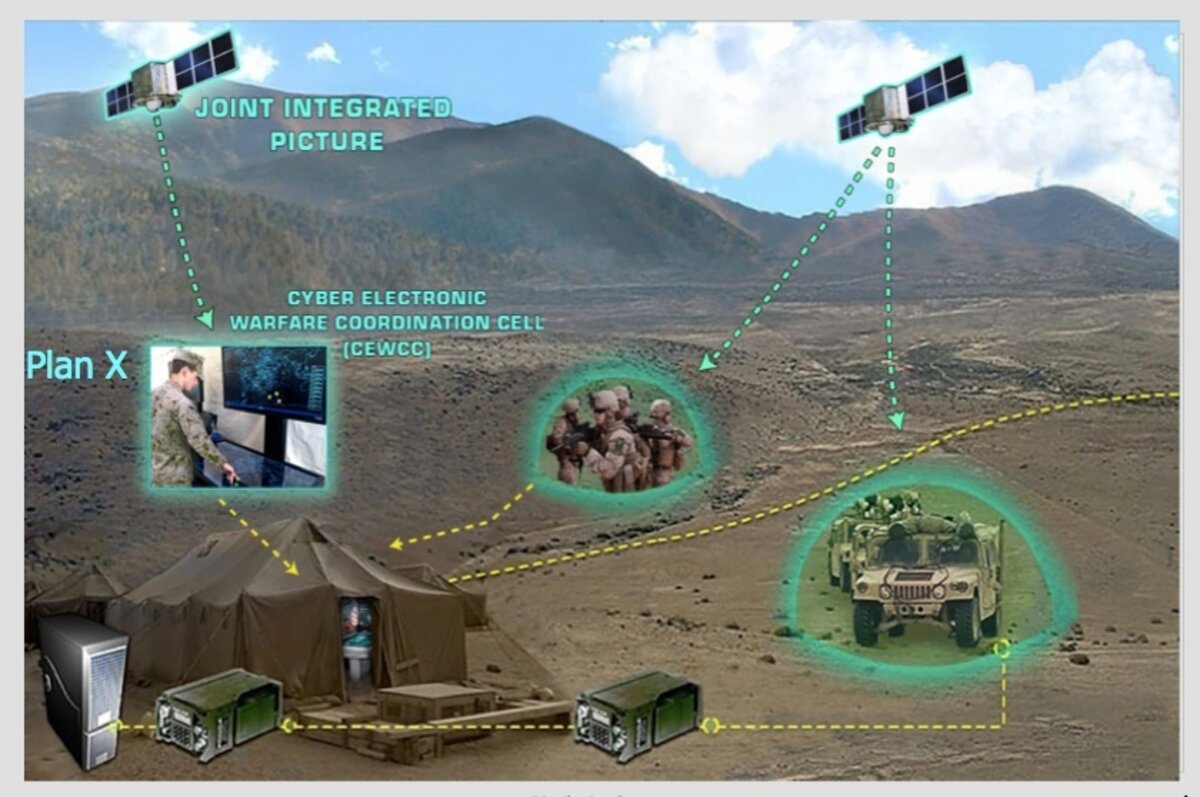
Pound envisions a Plan X system installed at every military installation and command across the world. This would send the entire picture of cyberthreats to Cyber Command to give them full awareness of everything on the military's online networks.
It would also be crucial on the battlefield, where soldiers often have Android devices, Humvees have computers inside them and drones flying overhead.
The military wants to know the status of those online devices at all times. It also wants to know if the connections go down.
Plan X will also help commanders plan missions. In traditional warfare, the specifications of different weapons -- and what damage they might cause – are fairly well known from the time they are built. So far, there's no equivalent for online attacks.
Or counterattacks.
Commanders could predict the potential damage caused by malicious attacks to make better decisions about the response, or, potentially, game out their own online operations by simulating them on the Plan X network.
DARPA is building Plan X with a Silicon Valley-style software development model.
As soon as new code is entered into the system – or an application needs testing – the operator would quickly simulate it on the National Cyber Range, a testbed for critical security research.
"That will spin up Windows boxes and Linux boxes and routers and things like that virtually, and deploy the app in the configuration it needs to be deployed to operate in the real world," Pound explained. They will test it "over and over again, introduce fault cases and figure out how it behaves."
If it works, it’s good for primetime. That process, from start to finish, is 72 hours.
That’s remarkably fast for the military’s typical development process, and that’s in part because the software development model DARPA is using in the program is closely modeled on those used by Silicon Valley companies.
"We call it continuous development, where every time theres a change in the system, every time theres an app added to the app store, it automatically goes through what are called ‘smoke tests,' " Pound says. As soon as the code is checked in, it will go through lots of testing. This is a far cry from the model the Pentagon has used in the past, where code was written and tested a few months later – and tested again back and forth sometimes for months after bugs were detected. "We’re doing that multiple times a day now."
Still, the fledgling program only started about 18 months ago. It’s set to finish in October 2016.
To ease the future transition to the military, DARPA researchers are already meeting with military personnel to loop them in on their progress, through hackathons and demonstrations, so they too can view the system’s progress and the agency can make sure their specific needs are addressed as they build it.
While the agency is building the system to support wide-scale development, the ultimate pace of the adaptation is up to the military – and it’s unclear at this point just how many Defense Department computers will actually use the platform in the early stages of transition.
You might own Plan X one day
By 2017, Cisco, the world's largest maker of network equipment, predicts every Internet user on the planet will have an average of five devices or connections. In addition to your Web-enabled TV, smartphone, and tablet, your air conditioner and refrigerator may be connected.
DARPA, which has a long history of building technology that enters the commercial market only to become staples of everyday life – including the basis for GPS technology and the software behind Apple's Siri – is building Plan X to be easily customizable.
"Wouldn’t it be great to have some system that gives you a real quick update status, everything on your LAN, your computer, your television, your cell phones as they’re floating around in your environment?" Pound says. "Think about giving people situational awareness through this invisible ephemeral space that’s very hard to conceptualize right now."
Of course, the US still needs hackers and subject matter experts to write code, Pound says. But everyone who has been hacked might appreciate a similar warning system to what the military is developing. "[We want to] democratize the visualization of networked things," Pound says.
What does that look like?
A dashboard on your kitchen counter could have a scaled-down version of Plan X to detect if your refrigerator is being hacked or your computer hijacked.
It could help cybersecurity professionals and companies, too. Imagine if, say, you’re a company under attack. You might be able to call a virtual cybersecurity operations help center. You could communicate “face to face” with help specialists with avatars in a virtual-reality.
Together, you could investigate the network and find the problems. Plan X, in the private sector, could be a game-changer for the cybersecurity industry.
If you want to geek out a little...
Here's an exclusive look at the storyboard DARPA commissioned from design company Massive Black.